Protect Your Data with a Secure Data Room

Overlooking data security can not only damage your business’s reputation but lead to legal issues and unexpected expenses. Much of the hassle could have been easily prevented with a reliable VDR.
Virtual data rooms can help you to ensure transparent business operations, build loyal and trusting relationships with clients, and protect your companies integrity and credibility.
What makes a virtual data room secure?
The level of virtual data room security relies on software security certifications, encryption protocols, and security features. There is a reason why data security regulations have become increasingly stringent — in today’s digital world, data is considered the most valuable resource.
A secure virtual data room solution is a wise investment for businesses dealing with sensitive client information, confidential financial data, and intellectual property.
The modern world makes companies face many unique issues we didn’t have even a decade ago. And one of such challenges is digital data security. Any business has to deal with enormous quantities of information, and its amount only increases. But the problem is not only with the management of data. Companies also need to protect it somehow because data leaks are extremely expensive and draining. In fact, they can ruin the reputation of the firm and, consequently, the business itself. That’s why the company starts to use specialized secure business software that guarantees 99% uptime of online data security. Thus, virtual data rooms became a vital tool for every company that needs a secure way to exchange documents with clients. Virtual data room is the most secure website for online deals; business software for work with highly confidential information that is confirmed and guaranteed by international organizations certificates.
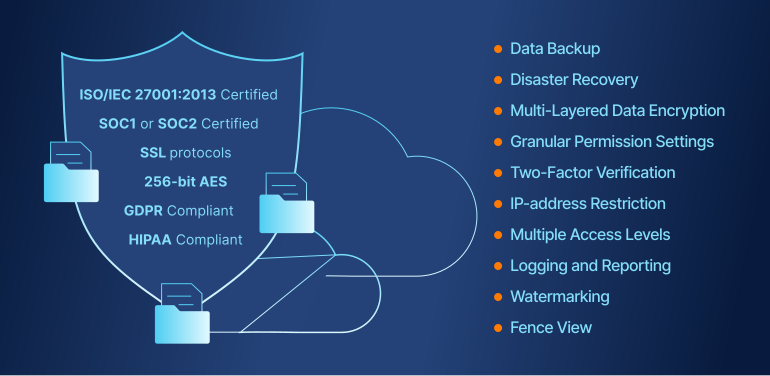
The most secure virtual data room providers annually confirm the quality of software and compliance with all information security standards. When choosing a secure VDR provider pay attention to the availability of certificates that ensure data room documents security:
- ISO/IEC 27001:2013 Certified Data Centres
- SSAE 16 SOC 1 and SOC 2
- GDPR Compliant
- HIPAA Compliant
These are the basic international standards each secure data room provider has to have. Before choosing a VDR provider customers should check the availability of listed certificates. Also, one of the vital advantages of the digital data room is that the VDR provider is responsible for online data security that is confirmed by the contract.
Required certifications for a secure VDR
The most secure data room software has many layers of security. Data security certification indicates what different compliance standards the software meets and is the most reliable proof of a data room’s security level. Choosing a certified data room provider will guarantee your data will be handled according to industry regulations.
Below are the most important security standards for virtual data rooms.
ISO/IEC 27001:2013
ISO/IEC 27001:2013 is one of the most important data room software standards (commonly referred to as ISO 27001) and the most popular, internationally recognized standard for information system security. An ISO 27001 certificate demonstrates the quality and reliability of software and shows that the company is committed to providing high-level security.
The standard asks for the implementation of more than just software and hardware security functions. It also requires setting out appropriate control mechanisms such as policies, processes, procedures, and organizational structures. The ISO 27001 requirements are generic and applicable to any organization dealing with an information security management system, not just virtual data rooms.
SSAE 16 SOC 1 and SOC 2
SOC 1 and SOC 2 are System and Organization Controls (SOC) defined by the American Institute of Certified Public Accountants (AICPA) regulating organizations that provide IT systems as a service to other businesses and individuals.
It is important not to mistake SOC2 as the updated version of SOC1. They are separate standards regulating different aspects of information system services: SOC 1 concerns Internal Control over Financial Reporting, while SOC 2 refers to Trust Services Criteria. SOC 1 specifically protects clients’ financial information, while SOC 2 applies to all other sensitive information — regardless of the client’s industry.
GDPR
The General Data Protection Regulation (GDPR) is an EU regulation for personal data protection, privacy, and integrity. GDPR covers data processing and also data exchange between the EU and countries outside the EU and EEA area.
GDPR requires any company that deals with individual personal information such as contracts, physical addresses, e-mail addresses, phone numbers, etc., to adhere to the GDPR data protection rules. Therefore, when choosing a virtual data room provider, a GDPR compliant software will ensure that data is processed legally, under GDPR rules, protecting individuals’ rights.
HIPAA
HIPAA, the Health Insurance Portability and Accountability Act of 1996, protects sensitive patient health information and applies to anyone with access to patient files. A virtual data room provider who is HIPAA compliant is the best choice for anyone in the health and R&D sector wanting to increase work efficiency and collaboration without sacrificing the security of individually identifiable patient health data.
Secure data room features
In addition to security standard compliance, VDRs offer a variety of security functions for an extra layer of protection. These features guarantee that data is being shared only with intended recipients in a secure manner.
Most valued security features include:
- Data encryption for files and messages. Encryption converts files and messages to a secure code before sharing them. Typically, file sharing services would encrypt messages, but secure VDRs can encrypt the documents themselves.
- Data backup. Using a virtual data room means that all of your files are not stored on a single server or computer but rather located in a virtual space accessible from any device. Therefore, in case a device is compromised by a virus, stops working, or gets lost, all your data will still be secure in your online data room.
- Customizable user permissions. A good VDR software allows the administrator to set granular user permissions, thus allowing the user to create multiple teams or user groups, each with a different level of access to files. For example, some documents can be set to be accessible only to management and auditors, while others, only to internal experts.
- The fence view feature lets you choose which part of the document will be visible to the user, keeping the rest of the content hidden.
- Remote shred (revoking access even after download). The remote shred feature ensures secure document retention even after downloads. You can revoke access to certain documents for users no longer working on the project. This function also helps facilitate a correct document disposal process as per data protection laws.
- Document expiration. Most VDRs allow the administrator to set document expiration times for invited third parties. This feature automatically revokes access after a set deadline.
- Two-factor authentication. This feature minimizes the risk of password theft, as it requires the user to verify their identity by providing two authentication factors, such as a password and a finger scan, face scan, or passcode sent to another device.
- Full audit trails. The administrator can access and review each user’s activity within the data room, including what files have been viewed and for how long, what files have been forwarded, downloaded, or printed, etc.
- IP-address restriction enables administrators to set user access permission based on a user’s IP address or range of IP addresses. The administrator can also limit the number of IP addresses used for logging in.
- An antivirus protection system ensures the scanning of all incoming documents for viruses as they are uploaded to the platform.
- Screenshot protection safeguards your document’s content if the user opens a screen capturing app on their device.
- A dynamic watermarking feature overlays a text or an image over your document contents, thus protecting your contents from unwanted sharing or use. You can overlay a watermark on all your documents at once.
- A secure spreadsheet viewer allows administrators to set multiple access options, allowing some users to modify formulas while others can only view and download a watermarked spreadsheet.
- Customer-managed encryption keys (key vault location). This function allows the user to set their own encryption key for data protection.
- The terms of access (NDA) feature asks anyone who is invited to your data room to agree not to disclose information covered by the terms of access, making the process of signing separate NDAs with each user more effective.
Many businesses think that they can stick to generic cloud services to store and exchange corporate documents. And that’s a big mistake because such platforms are not reliable enough to trust sensitive information. That’s why you should consider using a virtual data room instead.
VDR providers protect both the repository with documents and data transfer ways with the strongest 256-bit encryption. Thus, malefactors have no chances to break into the data room and steal or corrupt your corporate information. And that’s not the only method of data protection providers use.
A secure online data room will have two-factor authentication that will prevent unauthorized access. This technology will ask users to prove their identity not just by entering the login information. Usually, they will have to enter a code sent via an SMS or email upon logging in. But often vendors offer several options.
In addition to that, the manager of the data room can set different levels of access for users to decide what they can and cannot do with uploaded documents. Such a feature gives the business complete control over what’s going on in the secure data room and ensures privacy. Also, the administrator can track all the user activity – what documents did they access, what did they do with them, and for how long. This information allows for detecting suspicious activity in secure VDR. Moreover, it can give the business owner many valuable insights about the deal and the intentions of third parties.
The most secure data room providers allow users to set a document expiration for the accounts of invited third parties. It will protect the information by cutting access to the repository automatically when the deal is over. Also, some VDR vendors offer a remote data shredder that will be a lifesaver when certain accidents happen.
Customizable watermarks ensure that your documents can not be used by third parties. The secure data room allows customizing the watermarking settings. The administrator chooses the watermark view for example user’s name, IP address, date and time of access, logo. It helps to prevent the leakage of information within the company among employees.
Finally, virtual data rooms offer businesses detailed reports that can bring valuable insights. Studying these statistics entrepreneurs can see how well the company performs, and what they can do to make the next deal be even more successful. Also, reports are useful during the deal – they can help you make better data-driven decisions and be sure to keep data confidential.
How to choose the most secure virtual data room?
Virtual data room services in terms of security and functionality will differ from client to client, as their needs differ. For example, a well-known, secure VDR software with HIPAA certification might not be the best solution for businesses outside the healthcare industry. It is best to determine your own needs, know your options, and then compare data room offerings.
- To determine the secure virtual data room solution:
- Provide an overview of VDR provider ratings and reviews.
- Determine your specific industry and business needs, required security certification compliance, and desired security features.
- Narrow your search down to those VDR solutions with industry-specific security certifications and good reviews from previous and existing clients. Determine what security guarantees are provided in each tariff plan.
- Check out the list of secure data room services.
- Compare multiple offers based on their functionality and the price and make a confident decision.
- Do not settle; consider using free trial versions until you find one that suits your needs. Know that there are many other options on the market.
- Check out the contract, pay attention to the providers’ responsibilities.
- Choose the certified and reliable virtual data room software.
The virtual data room market is crowded with a lot of providers, but not all of them comply with international standards and requirements. It is best to consider the most rated and well-known VDR providers, as you can easily find information about the company and study the real reputation of the secure VDR software. It’s difficult to find relevant information about less well-known suppliers, so you will have to contact the supp
Final word
With the growing popularity of document digitization, the number of secure virtual data rooms providers is rapidly expanding. Of course, not all of them meet the desired standards, so it is important to be aware of this area to make the right choice.
Successful business interaction with a virtual data room is the key to your peace of mind and optimized company functioning. Hopefully, the information we have offered here will help you choose from the sea of providers and achieve the desired security of your data.